Frontline officers need direct access to terrorism-related data in order to detect and positively identify members of transnational terrorist groups. We are working to increase the amount of biometric data and battlefield information available to police.
Fighting terrorism through biometrics
Biometric data – such as facial images and fingerprints – can lead to the accurate identification of individuals using a false identity, thereby improving efforts to locate terrorists and carry out successful investigations and prosecutions.
We created Project First (Facial, Imaging, Recognition, Searching and Tracking) to help countries share biometric data on foreign terrorist fighters (FTFs) and other terrorist suspects.
Project First promotes the move from a ‘need to know’ to a ‘need to share’ culture. It aims to improve the identification and detection of terrorists and their affiliates by using the latest technology in digital image processing and facial recognition.
Local law enforcement officers are trained to use mobile equipment in order to record the biometric data of prison inmates convicted of terrorism-related offences. This data is then stored in INTERPOL databases, for example as Blue Notices which are international alerts to collect additional information about a person’s identity, location or activities in relation to a crime.
The data can also be searched against other INTERPOL databases, in particular the facial recognition system and fingerprints database, to positively identify individuals and their international movements.
Bridging battlefield and police investigations
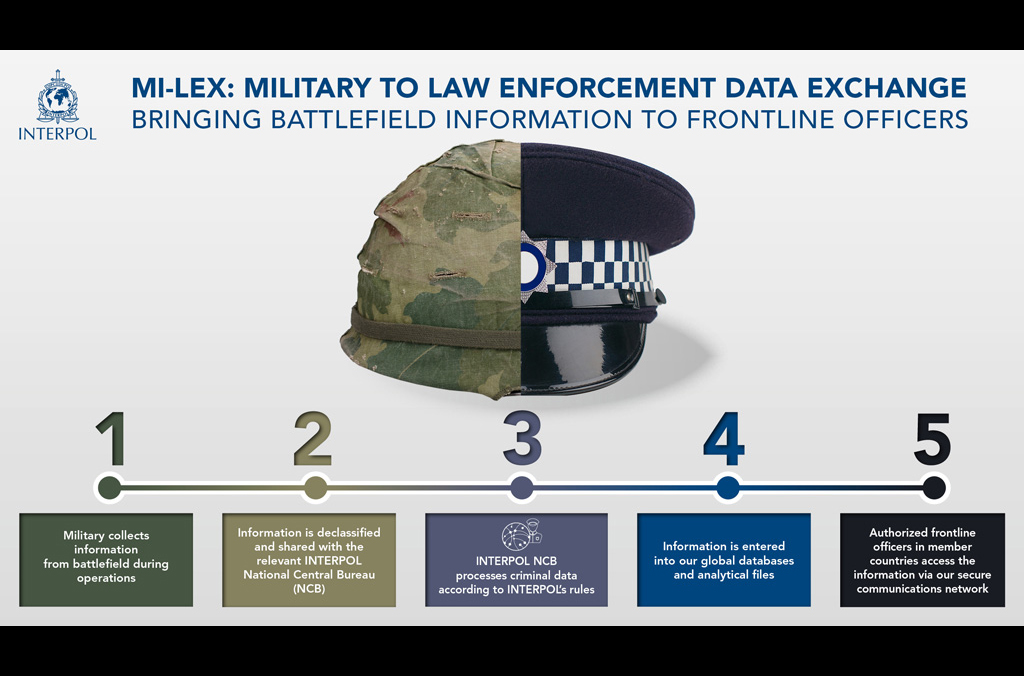
INTERPOL was the first international organization to develop and implement a military-to-police information exchange model (Mi-Lex). This puts information from conflict zones into the hands of law enforcement officers, to support police investigations and the prosecution process.
Military first responders can share declassified information collected from the battlefield with relevant INTERPOL National Central Bureaus who process the information according to our rules and enter it into o databases and analysis files. Authorized frontline users in member countries can then access the information via the I-24/7 network.
Regional focus
We run six regionally based initiatives to identify and dismantle terrorist networks.
Building on their individual successes, we are now reaching out further, to connect activities and intelligence between regions that traditionally have not worked closely together.

Related news

Border security threats focus of STOP operations in Africa
8 December 2023